Mon 04 December 2023:
Paying for things digitally is so common, most of us think nothing of swiping or tapping our card, or using mobile payments. While doing so is second nature, we may be more reluctant to provide card details over the phone.
Merchants are allowed to ask us for credit card details over the phone – this is perfectly legal. But there are minimum standards they must comply with and safeguards to protect consumer data.
So is giving your card details over the phone any more risky than other transactions and how can you minimise the risks?
How is my card data protected?
For a merchant to process card transactions, they are expected to comply with the Payment Card Industry Data Security Standard. This is a set of security requirements designed to protect cardholder data and the trillions of dollars of transactions each year.
Compliance involves various security measures (such as encryption and access controls) together with strong governance and regular security assessments.
If the information stored by the merchant is accessed by an unauthorised party, encryption ensures it is not readable. That means stealing the data would not let the criminals use the card details. Meanwhile, access controls ensure only authorised individuals have access to cardholder data.
Though all companies processing cards are expected to meet the compliance standards, only those processing large volumes are subject to mandatory regular audits. Should a subsequent data leak or misuse occur that can be attributed to a compliance failure, a company can be penalised at levels that can escalate into millions of dollars.
These requirements apply to all card transactions, whether in person, online or over the phone. Phone transactions are likely to involve a human collecting the card details and either entering them into computer systems, or processing the payment through paper forms. The payment card Security Standards Council has detailed guides for best practice:
A policy should be in place to ensure that payment card data is protected against unauthorised viewing, copying, or scanning, in particular on desks.
Although these measures can help to protect your card data, there are still risks in case the details are misplaced or the person on the phone aren’t who they say they are.
Basic tips for safe credit card use over the phone
If you provide card details over the phone, there are steps you can take to minimise the chance you’ll become the victim of fraud, or get your details leaked.
1. Verify the caller
If you didn’t initiate the call, hang up and call the company directly using details you’ve verified yourself. Scammers will often masquerade as a well-known company (for example, an online retailer or a courier) and convince you a payment failed or payment is needed to release a delivery.
Before you provide any information, confirm the caller is legitimate and the purpose of the call is genuine.
2. Be sceptical
If you are being offered a deal that’s too good to be true, have concerns about the person you’re dealing with, or just feel something is not quite right, hang up. You can always call them back later if the caller turns out to be legitimate.
3. Use secure payment methods
If you’ve previously paid the company with other (more secure) methods, ask to use that same method.
4. Keep records
Make sure you record details of the company, the representative you are speaking to and the amount being charged. You should also ask for an order or transaction reference. Don’t forget to ask for the receipt to be sent to you.
Check the transaction against your card matches the receipt – use your banking app, don’t wait for the statement to come through.

Cancelling your card is a hassle, but it’s the best way to prevent further funds being stolen from your account. Eduardo Soares/Unsplash
Virtual credit cards
In addition to the safeguards mentioned above, a virtual credit card can help reduce the risk of card fraud.
You probably already have a form of virtual card if you’ve added a credit card to your phone for mobile payments. Depending on the financial institution, you can create a new credit card number linked to your physical card.
Some banks extend this functionality to allow you to generate unique card numbers and/or CVV numbers (the three digits at the back of your card). With this approach you can easily separate transactions and cancel a virtual card/number if you have any concerns.
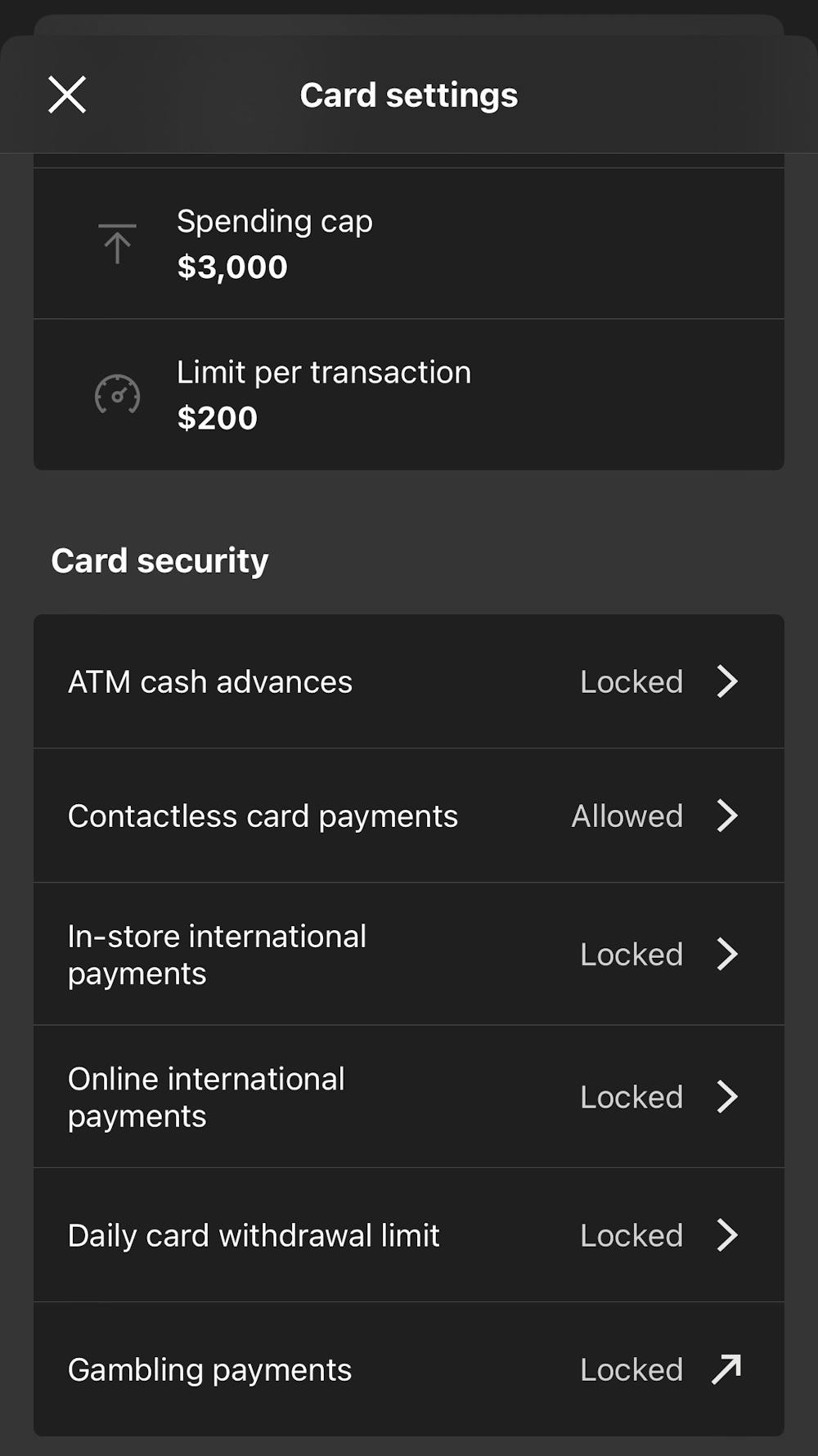
What to do if you think your card details have been compromised or stolen?
It’s important not to panic, but quick action is essential:
- call your bank and get the card blocked so you won’t lose any more money. Depending on your situation, you can also block/cancel the card through your banking app or website
- report the issue to the police or other relevant body
- monitor your account(s) for any unusual transactions
- explore card settings in your banking app or website – many providers allow you to limit transactions based on value, restrict transaction types or enable alerts
- you may want to consider registering for credit monitoring services and to enable fraud alerts.
So, should I give my card details over the phone?
If you want to minimise risk, it’s best to avoid giving card details over the phone if you can. Providing your card details via a website still has risks, but at least it removes the human element.
The best solution currently available is to use virtual cards – if anything goes wrong you can cancel just that unique card identity, rather than your entire card.
Authors:
![]()
Paul Haskell-Dowland
Professor of Cyber Security Practice, Edith Cowan University
Professor Paul Haskell-Dowland is the Professor of Cyber Security Practice and Associate Dean for Computing and Security in the School of Science at Edith Cowan University, Perth, Australia. Paul has delivered keynotes, invited presentations, workshops, professional development/training and seminars across the world for audiences including RSA Security, ITU and IEEE. He has appeared on local, national and international media (newspaper, radio and tv) commenting on current cyber issues with a global audience reach of more than 1.5 billion people. His contributions through articles published in The Conversation have reached over 3 million readers – joining the top-50 all-time authors in Australia/New Zealand (top-10 in 2021). Paul has more than 20 years of experience in cyber security research and education in both the UK and Australia.
Paul is the Working Group Coordinator and the ACS/Australian Country Member Representative to the International Federation for Information Processing (IFIP) Technical Committee 11 (TC11 – Security and Privacy Protection in Information Processing Systems); the secretary to IFIP Working Group 11.1 (Information Security Management); a member of the ACS Cyber Security Committee; a Senior Member of the IEEE and the ACS (Certified Professional); and, a Fellow of the Higher Education Authority, BCS and the Australian Information Security Association.
Paul can be followed on Twitter (@pdowland).
______________________________________________________________
![]()
Ismini Vasileiou
Associate Professor, De Montfort University
Dr. Ismini Vasileiou, an Associate Professor of Information Systems (FBCS, SFHEA), brings a wealth of experience and expertise to the field of Computer Science and related disciplines, particularly in strategic leadership. Throughout her career, Dr. Vasileiou has been actively involved in creating strategic partnerships, conducting research, and making significant contributions in areas such as Cyber Education, Human Factors, and Social Engineering.
One of Dr. Vasileiou’s primary areas of focus is the Digital and Cyber Skills agenda, where she plays a vital role as a strategic leader. Her emphasis on pedagogical development across various disciplines is aimed at fostering knowledge transfer and enterprise. Taking an interdisciplinary approach to Digital Transformation, Education, Awareness, and Training, Dr. Vasileiou views Cyber as a meta-discipline that permeates multiple domains.
Beyond her academic roles, Dr. Vasileiou serves as the UKC3 East Midlands Cyber Security Director, further highlighting her expertise and influence in the field. Her knowledge and insights have made her a highly sought-after keynote speaker on topics such as Digital Transformation in Higher Education, Social Engineering, and Cyber Education.
______________________________________________________________
FOLLOW INDEPENDENT PRESS:
WhatsApp CHANNEL
https://whatsapp.com/channel/0029VaAtNxX8fewmiFmN7N22
![]()
TWITTER (CLICK HERE)
https://twitter.com/IpIndependent
FACEBOOK (CLICK HERE)
https://web.facebook.com/ipindependent
Think your friends would be interested? Share this story!





